
January 2005
The LawsonGuru Letter is a free periodic newsletter containing provocative commentary about issues important to the Lawson Software community. The LawsonGuru Letter is published by-and is solely the opinion of-John Henley of Decision Analytics. Visit Decision Analytics at https://www.danalytics.com. For subscription information, see the bottom of this message.
The LawsonGuru Letter is not affiliated with Lawson Software.
In this issue:
1. Reporting, Part 8: Security in Lawson Reporting Services
2. First Look: Lawson Surgical Instrument Management
3. Worthwhile Reading
4. Lawson Tips & Tricks
1. Reporting, Part 8: Security in Lawson Reporting Services
Returning to our multi-part series on reporting, this month we'll focus on the security that is implemented in Lawson Reporting Services. One of the underlying goals for a reporting solution is that it must adequately support your security requirements. In a nutshell, you need to control who can have access (authentication), as well as what data can be accessed (authorization). This is a tough task to implement, particularly the authorization part. Your level of success (or failure) can vary greatly depending on the solution, as well as your security requirements (and of course, your flexibility in adhering to them).
Authentication vs. Authorization
Application security is comprised of two components:
- Authentication deals primarily in the determination by the application that a user is who they say they are. This generally involves challenging the user for user id and password credentials before allowing them access to the system, and then checking those credentials to ensure they are valid before letting the user continue.
For authentication, LRS (via the Framework Services in Lawson Reporting Suite) supports a plug-in architecture where several different providers are supported. This leverages your existing architecture(s) rather than duplicating some portion of them in LRS. LRS can be configured to use a variety of different authentication providers:
|
Provider
|
Users
|
Security Classes
|
|
Lawson Environment/IOS
|
Yes
|
Yes
|
|
LDAP
|
Yes
|
Yes
|
|
Microsoft Active Directory
|
Yes
|
Yes
|
|
Text file (flat file)
|
Yes
|
Yes
|
|
Relational Table
|
Yes
|
Yes
|
|
Lawson Services Automation
|
Yes
|
No
|
Note: Since LDAP and Active Directory implementations can vary widely, LRS cannot fully support all possible configurations.
- Authorization specifies what objects a user can see, and what they can do with those objects. For example, authorization determines what departments or employees a user can see. Authorization also specifies what a user can do with an object, such as whether a user has the right to view or schedule a certain report or not.
Authorization in LRS is split into two different pieces:
- The modules within the Reporting Suite control the rights associated with specific reporting objects:
Report Contents
When publishing a report or other document to Reporting Services, the publisher has the ability to select users that can view the report, and can specify a username and password for the populating the report content. If a username and password is provided, the report will always be run by that user with their security access (LAUA/IOS security if using DME). The assumption here is that object security is sufficient.
If the publisher does not specify a username and password when publishing the report, each user-at runtime-will be prompted for a login/password and the report will be refreshed. If the data source connection is the Lawson OLEDB Provider, LAUA/IOS security will be enforced. If the connection is native (e.g. ODBC), database security is used.
Lawson DrillAround
Drill Around from a published Crystal report requires portal (or IOS, if running outside of the Portal) authentication. If the user is logged in to the Lawson Portal, they will not be prompted to log in again. In the event that the user is running LRS outside the Lawson Portal, they will receive a login dialog where they will need to provide their username and password. This login will be authenticated against IOS/Logan.
- Access to individual data items that are used in report content (such as departments, employees, projects, etc.) are controlled by the applications and databases that "own" them. For instance, the Lawson HR system controls who can see what employees. Lawson General Ledger (through the Lawson Environment) controls who can see what departments. These are generally referred to as security filters:
Lawson OLEDB Provider
Connects to the Lawson Database using Lawson IOS authentication; authentication happens when refreshing report data. When using DME to query the Lawson database, IOS and LAUA security is enforced. Where appropriate, data is filtered by IOS based on 1 of 6 different WEBUSER (RD30) settings: Company, Customer, Employee, Buyer, Requester, and/or Vendor. When accessing Standard Report output, LAUA security is not enforced and you must rely on object level security.
ODBC/Native Database
This connection relies completely on database security. This connection type is much faster than DME and the queries can be much more complex. (For more information on the differences between using the Lawson OLEDB Provider and native database providers, see https://www.danalytics.com/guru/letter/archive/2004-08.htm.)
Parameter Pages
Parameter pages can use a hybrid approach, e.g. a parameter page can contain DME calls to provide a list of valid values for parameters that are then presented to the user. The selection of a parameter value then filters the results that are presented to the user. This approach requires the report to refresh but because the report query is done with ODBC, it runs more efficiently. Reporting Services provides the parameter page with the id of the user who is making the request. It is up to the parameter page itself to decide how to authenticate the user and satisfy the request. In the case of using Lawson DME to populate a parameter list, if the user is not currently logged into the Lawson Portal, they will be challenged for Lawson login information, regardless of the authentication provider used.
Summary
As you can see, the topic of security within Lawson Reporting Services (and overall as part of the Lawson Report Suite) can be a complicated one. In a nutshell, the security model can be summed up this way: Security on the data items themselves (departments, employees, etc.) is controlled by the underlying applications that Reporting Services queries to provide various report content. Access to those objects (i.e., the reports themselves) is controlled by the Reporting Suite modules (Reporting Services, Smart Notification, Scorecard / Analytics, and Process Flow). Authentication and authorization is accommodated by leveraging existing security providers (i.e. LDAP, IOS/LAUA, etc.) to eliminate the need to reinvent yet another security layer within LRS.
2. First Look: Lawson Surgical Instrument Management (SIM)
Over the past two months (see https://www.danalytics.com/guru/letter/archive/2004-10.htm and https://www.danalytics.com/guru/letter/archive/2004-11.htm) we've looked at two of the new Lawson products-acquired from Apexion Technologies-that make up Lawson's Mobile Supply Chain Suite:
? Mobile Par & Cycle Count (MPC)
? Receiving and Delivery Tracking (RAD)
This month we'll complete this series by looking at Surgical Instrument Management (SIM).
According to Lawson, the typical hospital Operating Room handles 13,000 cases annually, and generates 50% of a hospital's revenue. In the process, the OR manages 1600 unique instrument tray configurations, with an aggregate value of $2-4 million dollars, and requires 20-30 FTEs just for instrument management.
Lawson's new Surgical Instrument Management (SIM) product is aimed at reducing the manpower and costs associated with managing these instrument trays.
|
Why use SIM?
- Ensure that correct items and trays are available when and where needed
- Increase staff performance, lower instrument costs, and reduce surgery delays
- Time wasted on instrument hunts
- Complex and inconsistent count sheets
|
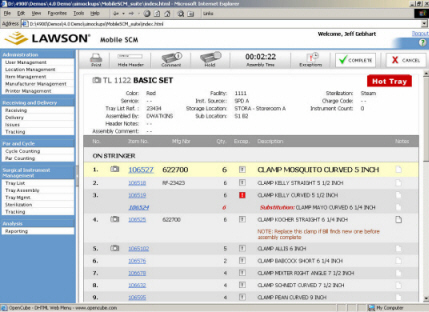 |
The SIM Cycle
SIM takes a workflow approach to instrument management (notice that I did NOT say Process Flow). Instrument trays cycle between the following areas:
- Operating Room
- Decontamination
- Tray Assembly
- Sterilization
- Stock Room
|
Key SIM Features:
Tray Assembly
- Find and view count sheets
- Record and highlight exceptions to instrument sets
- Print count sheets and barcode labels, including exception labels
Count Sheet Management
- Edit items and count sheets with version control
- Associate count sheets with unique trays
Tray Tracking
- Locate trays using most online computers
- Track trays and peel packs as they are moved
Sterilization
- Receive warnings about deviations in sterilization procedures
- Record sterilization contents, mechanical results and biological/chemical test information
Case Picking
- Assign trays to cases and case carts
- Capture and verify tasks with barcode scanning
Tracking and Reporting
- Run standard reports on staff productivity and tray standardization
- Can be integrated with Lawson Reporting Suite
Integration
- Integrates with the item master in Lawson Supply Chain Management
- Interfaces to leading operating room management systems
- Supports multiple facilities and locations
Mobile Technology Platform
- Uses the Microsoft Windows CE/Pocket PC operating system
- Symbol 8846 - Pocket PC
- Dolphin 7400 - Windows CE
- Wireless (802.11b) technology, supporting 128-bit encryption
- Supports multiple transmission modes, including real-time wireless, intermittent wireless and cradle-based synching
- Handhelds can be used for any Windows-CE application-they aren't dedicated to Lawson
- Lawson 8.0.3 Environment & 8.0.3 Applications
The Bottom Line
This is certainly an interesting product for Lawson, since it effectively moves them out of the back office, and onto the front lines. No, it's not really a life-or-death application, but the question for you will be: 'Do you trust Lawson enough to integrate them into your patient care delivery system??
+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
- QUOTE OF THE ISSUE -
?Those who dream by day are cognizant of many things which
escape those who dream only by night.?
- Edgar Allan Poe
+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
3. Worthwhile Reading
The Future of Software
The sector that produces most of today's software probably will look dramatically different in just a few years.
Information Week, December 6, 2004
http://www.informationweek.com/1017
The 2004 Money Issue of CIO
This special edition of CIO magazine looks at all things financial related to being a CIO.
CIO Magazine, Fall/Winter 2004
http://www.cio.com/archive/money/index.html
Is this the end of IT as we know it?
If you believe the hype, in a few years all enterprise software will be delivered as a service. At the least, you'll have the luxury of outsourcing many commodity apps
Infoworld, November 26, 2004
http://www.infoworld.com/article/04/11/26/48FEhosted_1.html
The Big Picture: Oracle-PeopleSoft Battle's Side Effect
It's hard to argue with SAP's strategy when tech pros crave depth.
Information Week, November 29, 2004
http://www.informationweek.com/story/showArticle.jhtml?articleID=54200560
4. Lawson Tips & Tricks
Share your tips. Send them to mailto:letter-tips@lawsonguru.com.
How to auto-complete partially-typed function names in the Crystal Formula Editor
(This one's actually a Crystal Reports tip I received in a Business Objects newsletter; since many Lawson users are also Crystal users, I decided to pass it along. By the way, wouldn't it be nice if Lawson had this feature in the Script editor in Design Studio?)
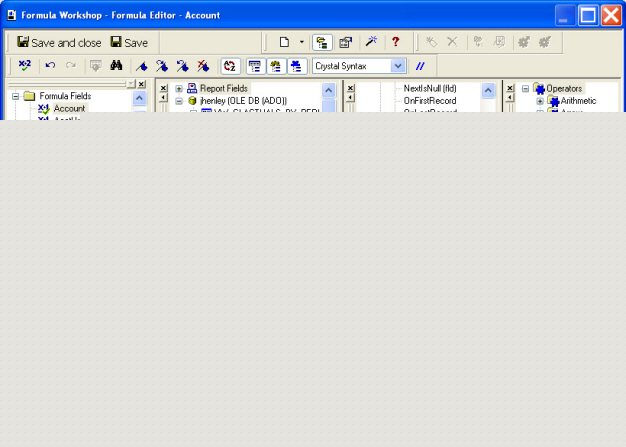
In the Formula Editor in the Crystal Reports Designer, how do you get partially-typed function names to auto complete? For example, if you type the first part of a function name, how do you get the rest of the function name to appear?
In the Formula Editor there is a method to auto complete partially-typed function names. This is similar to Microsoft's Intellisense feature in Visual Basic (as well as VBA in Excel and Access.)
After typing the first part of the function name, press CTRL + SPACEBAR to have the function name complete automatically. For example, if you type "WhilePrintingRe" and press CTRL + SPACEBAR, "WhilePrintingRecords" appears.
If there are multiple function names that match the partially-typed function name, a drop-down list of those functions names appears:
The LawsonGuru Letter is a free periodic newsletter providing provocative commentary on issues important to the Lawson Software community. The LawsonGuru Letter is published by--and is solely the opinion of--John Henley of Decision Analytics. Visit Decision Analytics at https://www.danalytics.com.
To subscribe, visit https://www.danalytics.com/guru/letter/
Copyright © 2005, Decision Analytics. All rights reserved. Please share The LawsonGuru Letter in whole or in part as long as copyright and attribution are always included.
Decision Analytics is an independent consultancy, focusing on Lawson technical projects, and specializing in customization/modification, data conversion, and integration/interfaces. Please visit https://www.danalytics.com for more information.
Decision Analytics. Integrating Lawson with the Real World.